Amazon Virtual Private Cloud (VPC)
Table of contents
- Notice
- What is Amazon VPC?
- AWS region
- How to create a VPC
- How to set up subnets
- How to set up an internet gateway
- How to set up a route table for the internet gateway
- How to allocate an elastic IP address
- How to set up a NAT gateway
- How to set up a route table for the NAT gateway
- Reference
1. Notice
- A guide for setting the Amazon Virtual Private Cloud (Amazon VPC)
- The name of region is Asia Pacific (Seoul) and the corresponding code is ap-northeast-2 [1].
- I refer to the Amazon VPC as VPC.
- I recommend that you should ignore the commented instructions with an octothorpe, #.
- I recommend that you should fill in the appropriate letters between the parentheses, <>.
2. What is Amazon VPC?
Amazon VPC enables you to launch Amazon Web Services resources into a virtual network you’ve defined. This virtual network resembles a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS [2]. You can check the Amazon VPC in details on the Amazon Virtual Private Cloud (VPC) [2].
Among the components of the VPC [3], we should set up the following components for the Amazon Elastic Kubernetes Service (EKS)
| No. | Component | Definition |
|---|---|---|
| 1 | Virtual private cloud (VPC) [3] | A virtual network dedicated to your AWS account. |
| 2 | Subnet | A range of IP addresses in your VPC. |
| 3 | Route table | A set of rules, called routes, that are used to determine where network traffic is directed. |
| 4 | Internet gateway | A gateway that you attach to your VPC to enable communication between resources in your VPC and the internet. |
| 5 | Elastic IP | An Elastic IP address is a static IPv4 address designed for dynamic cloud computing. |
| 6 | NAT gateway | A managed AWS service that allows Amazon Elastic Compute Cloud (EC2) instances in private subnets to connect to the internet, other VPCs, or on-premises networks. |
3. AWS region
As far as I mentioned in the Section 1. Notice, please note that the region and corresponding code are as follows:
- Region: Asia Pacific (Seoul)
- Code: ap-northeast-2
You can find more information about the regions and zones on the Regions and Zones [1].
4. How to create a VPC
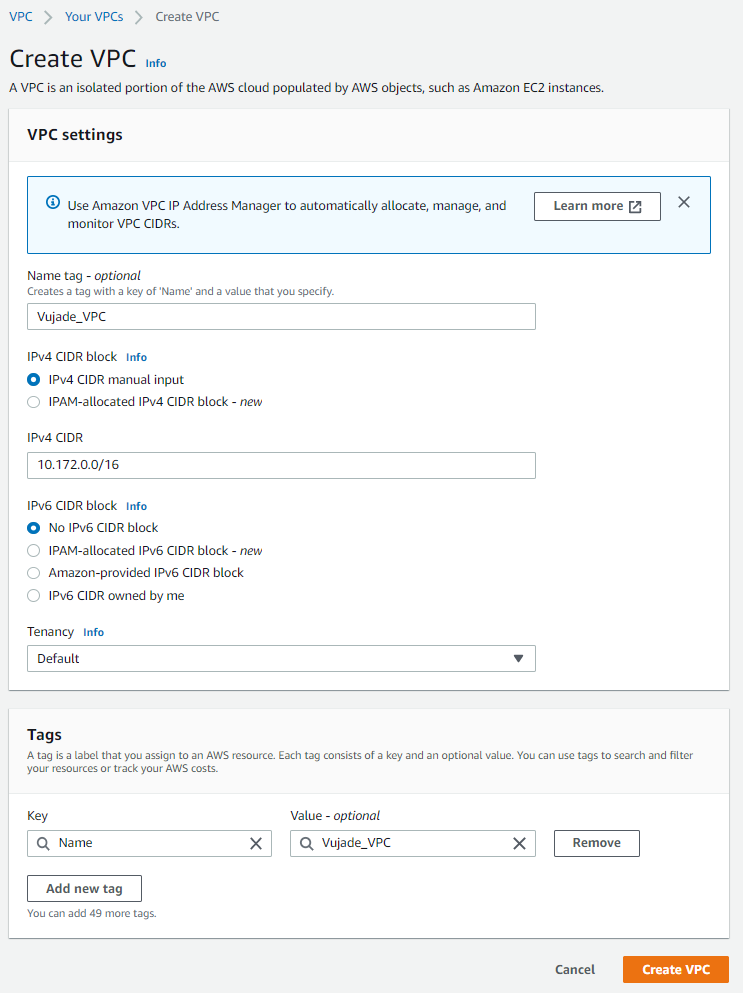
You can create a VPC on the Your VPCs as shown in Fig. 1.
You can define the name of VPC that will be created at the Name tag - optional. When you type text in the Name tag - optional,
the Value - optional field will automatically be filled with the same text. In this case,
I use the Name tag - optional and IPv4 CIDR for the created VPC as Vujade_VPC and 10.172.0.0/16, respectively.
Please note that you can add additional tag for the older version of the cluster [4] as follows. In this case, the tag is not required because the considered version of the cluster is 2.21.
- Key: kubernetes.io/cluster/<cluster-name>
- Value: shared
5. How to set up subnets
I recommend you should create public and private subnets. Please note that the data plane and management plane of the Amazon EKS are on the private subnets. Before proceeding with how to set up subnets, I would like to point out two important things:
- Amazon EC2 instance type in availability zone
- Tagging for load balancers or ingress controllers in the Amazon EKS
Some availability zones do not support particular instance types. Thus, if you receive the error “Your requested instance type is not supported in your requested Availability Zone”, you should determine which availability zones support your instance type [5]. In this case, a g4dn.xlarge instance is supported in ap-northeast-2a and ap-northeast-2c.
- EC2 instance type: g4dn.xlarge
- Region: Asia Pacific (Seoul), ap-northeast-2
- Availability zone: A and C
Please note that you should create a new tag if you hope to use load balancers or ingress controllers in the Amazon EKS [6]. In other words, the key and value for the tag are as follows:
- key: kubernetes.io/role/internal-elb
- value: 1
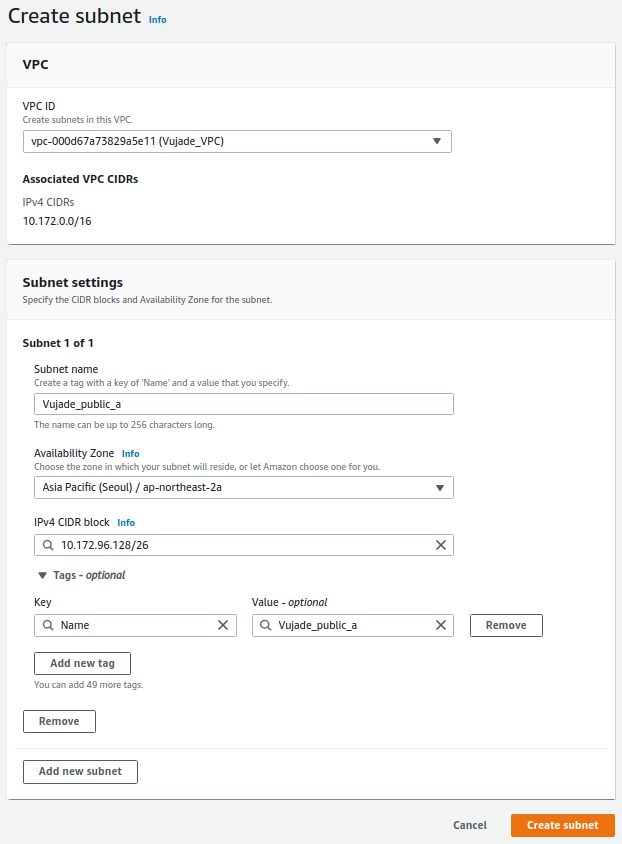
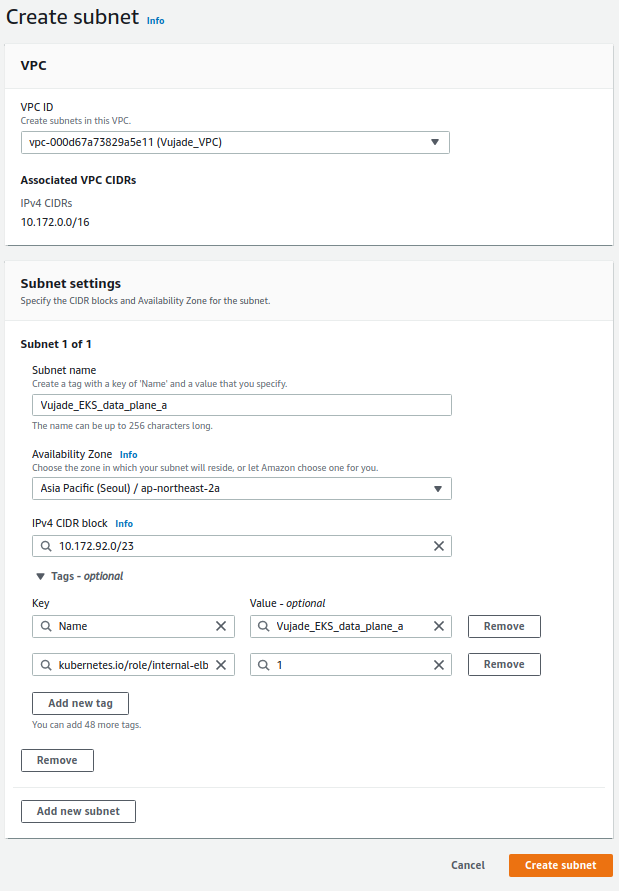
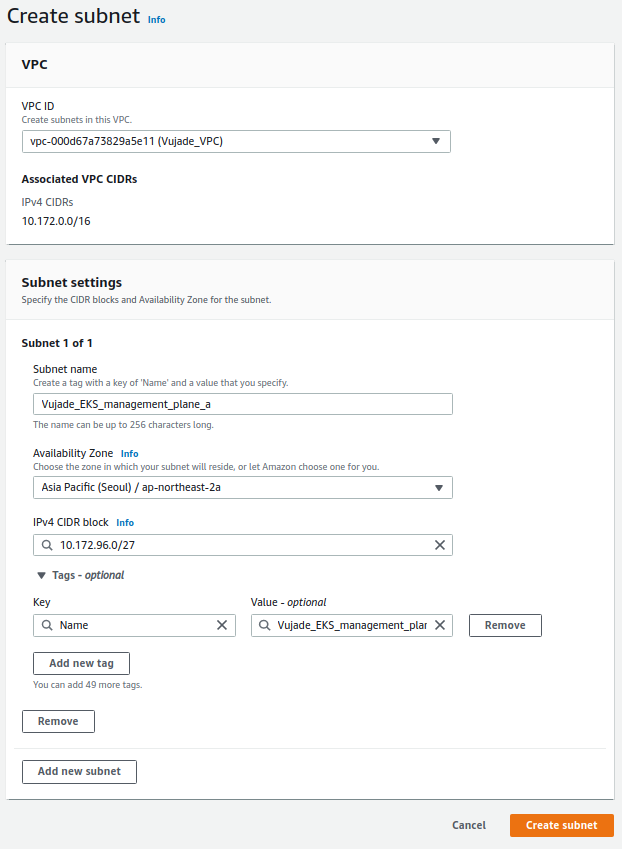
Fig 2 shows configurations for creating public subnet and private subnets for the data and management plane. Please note that subnets for the data plane have additional tag that is mentioned above.
The entire subnet configurations are as follows:
| No. | Kinds | VPC ID | Subnet name | Availability Zone | IPv4 CIDR block | Tags |
|---|---|---|---|---|---|---|
| 1 | Public | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_public_a | Asia Pacific (Seoul) / ap-northeast-2a | 10.172.96.128/26 | Name: Vujade_public_a |
| 2 | Public | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_public_b | Asia Pacific (Seoul) / ap-northeast-2b | 10.172.96.192/26 | Name: Vujade_public_b |
| 3 | Public | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_public_c | Asia Pacific (Seoul) / ap-northeast-2c | 10.172.98.0/26 | Name: Vujade_public_c |
| 4 | Private (Data plane) | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_EKS_data_plane_a | Asia Pacific (Seoul) / ap-northeast-2a | 10.172.92.0/23 | Name: Vujade_EKS_data_plane_a; kubernetes.io/role/internal-elb: 1 |
| 5 | Private (Data plane) | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_EKS_data_plane_c | Asia Pacific (Seoul) / ap-northeast-2c | 10.172.94.0/23 | Name: Vujade_EKS_data_plane_c; kubernetes.io/role/internal-elb: 1 |
| 6 | Private (Management plane) | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_EKS_management_plane_a | Asia Pacific (Seoul) / ap-northeast-2a | 10.172.96.0/27 | Name: Vujade_EKS_management_plane_a |
| 7 | Private (Management plane) | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_EKS_management_plane_b | Asia Pacific (Seoul) / ap-northeast-2b | 10.172.96.32/27 | Name: Vujade_EKS_management_plane_b |
| 8 | Private (Management plane) | vpc-000d67a73829a5e11 (Vujade_VPC) | Vujade_EKS_management_plane_c | Asia Pacific (Seoul) / ap-northeast-2c | 10.172.96.64/27 | Name: Vujade_EKS_management_plane_c |
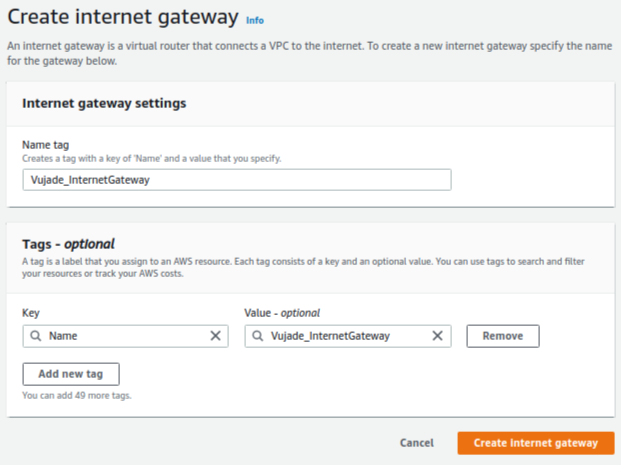
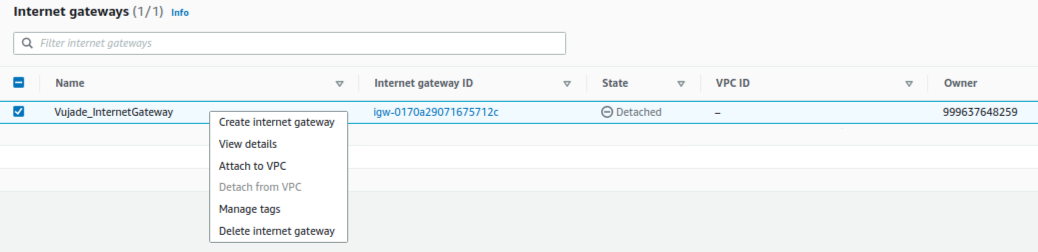
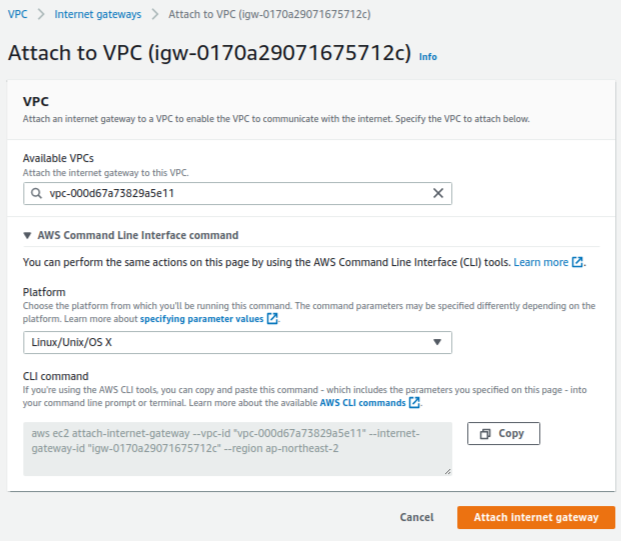
6. How to set up an internet gateway
You should create an internet gateway for public subnets as shown in Fig. 3. Please note that you should attach the created internet gateway to the corresponding VPC.
7. How to set up a route table for the internet gateway
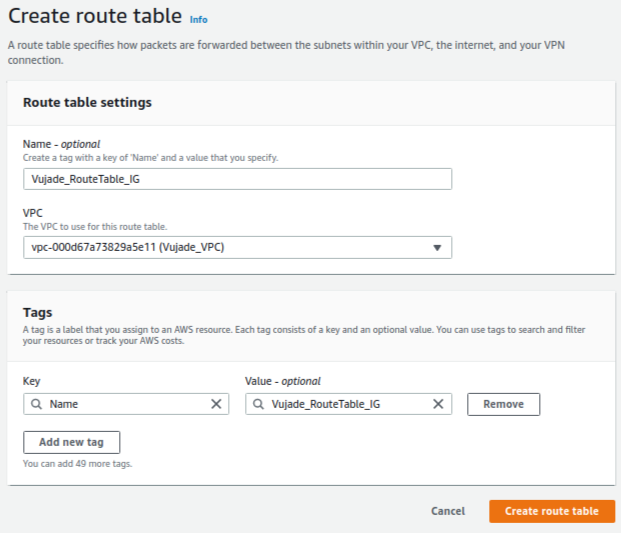
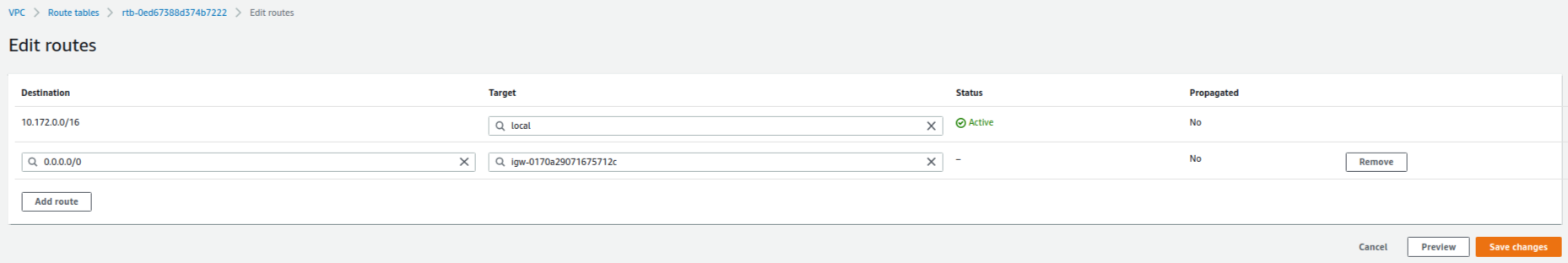
Please note that you should set up two route tables for an internet gateway and a Network Address Translation (NAT) gateway which corresponds to public and private subnets, respectively. In this section, I introduce how to set up a route table for the created internet gateway. The way to install a route table for the NAT gateway is addressed in the Section 10. How to set up a route table for the NAT gateway.
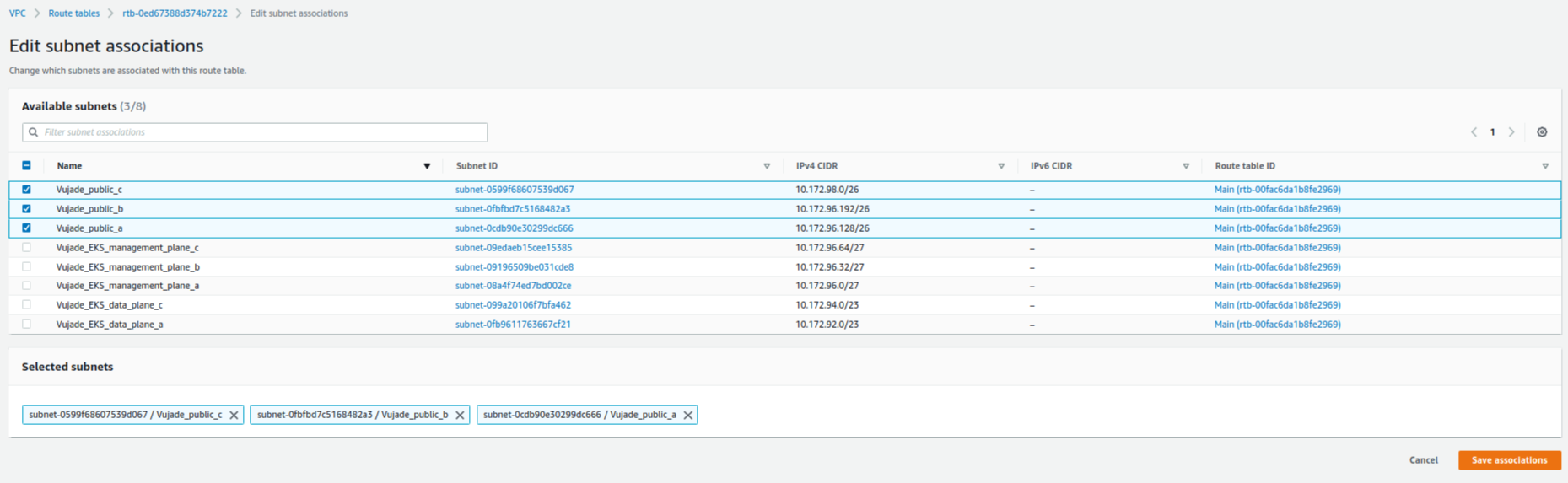
Fig. 4 shows how to set up a route table for the internet gateway. You should edit route tables and subnet associations after creating the route table.
8. How to allocate an elastic IP address
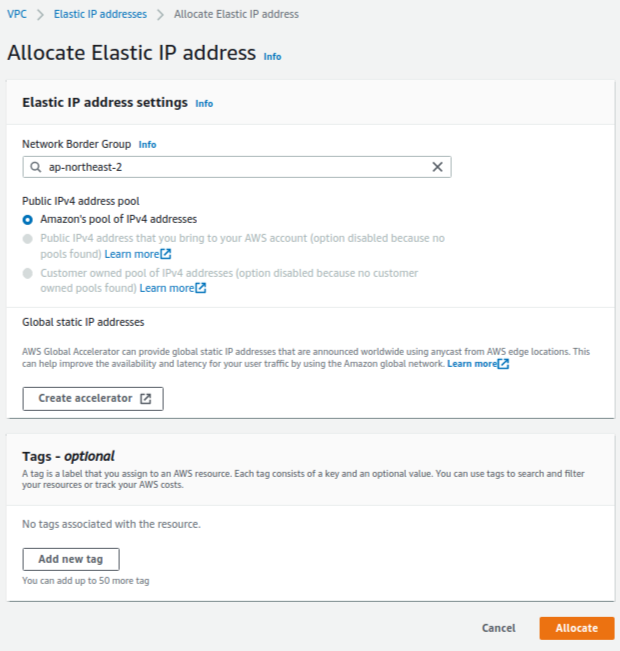
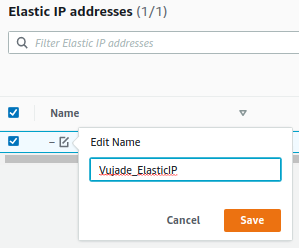
You should allocate an elastic IP address that is required when creating a NAT gateway in the Section 10. How to set up a route table for the NAT gateway. I recommend that you should modify the name of the allocated elastic IP address after getting the elastic IP address as shown in Fig. 5.
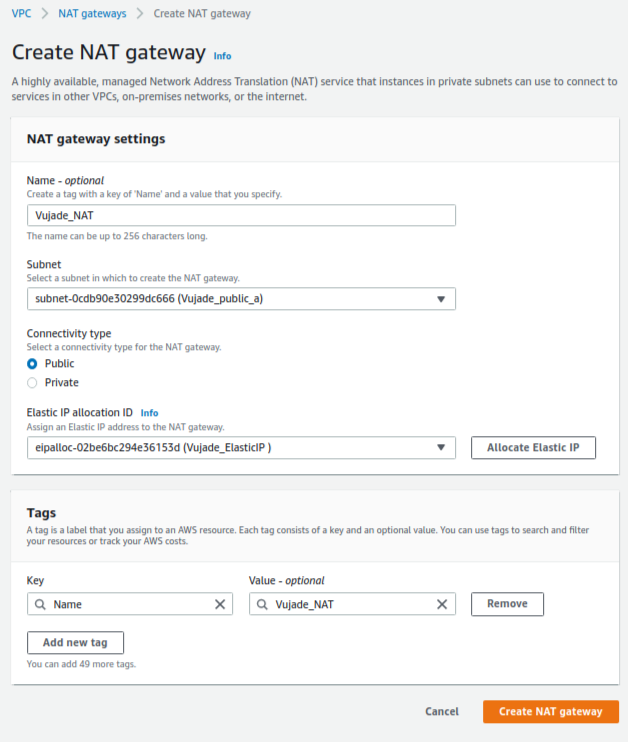
9. How to set up a NAT gateway
You can easily set up a NAT gateway as shown in Fig. 6. I recommend that you should set a subnet and an elastic IP allocation ID to the created resources. Especially, the recommend subnet is a public subnet in the availability zone A.
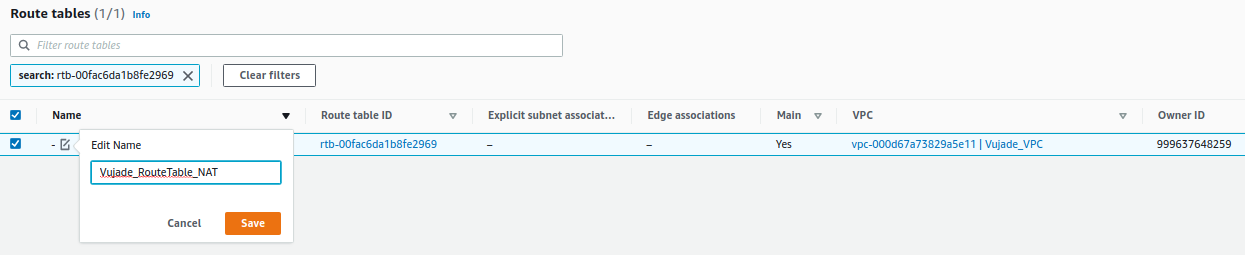
10. How to set up a route table for the NAT gateway
A route table for the NAT gateway has been already created. Thus, you can first find the created route table for the NAT gateway with the name of the VPC field. After finding the created route table, you can change the name of the route table and should edit route table as shown in Fig. 7.
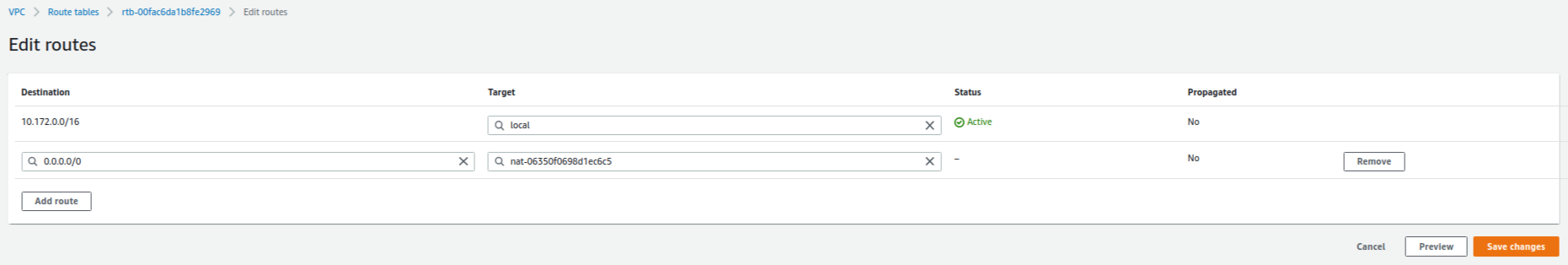
11. Reference
- Regions and Zones
- Amazon Virtual Private Cloud (VPC)
- What is Amazon VPC?
- Cluster VPC and subnet considerations - Subnet tagging
- Why am I receiving the error, Your requested instance type is not supported in your requested Availability Zone, when launching an EC2 instance?
- How can I tag the Amazon VPC subnets in my Amazon EKS cluster for automatic subnet discovery by load balancers or ingress controllers?